| Implemenation Step | Details | Technical Notes |
|---|---|---|
Understanding SAML based SSO for CompliSpace PolicyPlus
The following process explains how a user logs into the CompliSpace PolicyPlus application through an organisation’s, SAML based SSO service.
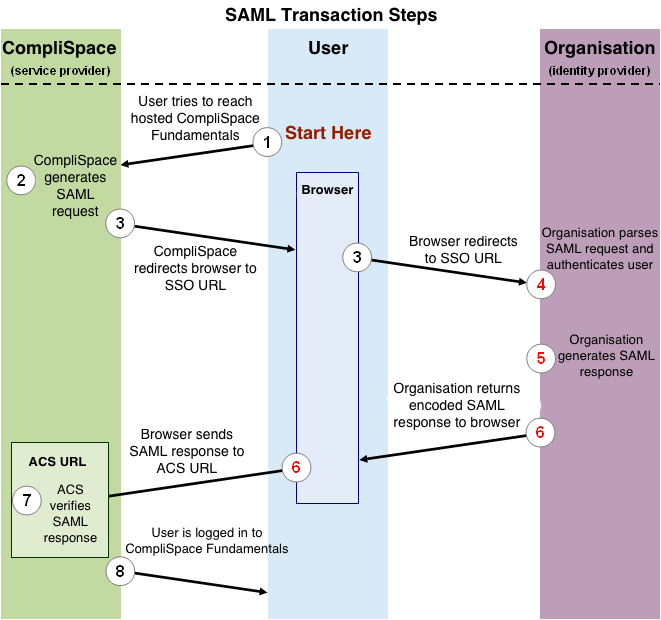
Figure 1, shown below, illustrates the process by which a user logs in to the CompliSpace PolicyPlus application through a SAML based SSO service. The numbered list that follows the image explains each step in more detail.
Note: Before this process takes place, the organisation must provide CompliSpace with the metadata XML for their IdP. CompliSpace will also provide the organisation the metadata XML for the PolicyPlus SP.
Figure 1: Logging in to CompliSpace PolicyPlus using SAML
This image illustrates the following steps:
- The user attempts to reach the CompliSpace PolicyPlus application.
- CompliSpace generates a SAML authentication request. The SAML request is encoded and embedded into the URL for the organisation’s SSO service. The RelayState parameter containing the encoded URL of the CompliSpace PolicyPlus site that the user is trying to reach is also embedded in the SSO URL. This RelayState parameter is meant to be an opaque identifier that is passed back without any modification or inspection.
- CompliSpace sends a redirect to the user’s browser. The redirect URL includes the encoded SAML authentication request that should be submitted to the organisation’s SSO service.
- The organisation decodes the SAML request and extracts the URL for both CompliSpace’s ACS (Assertion Consumer Service) and the user’s destination URL (RelayState parameter). The organisation then authenticates the user. Organisations could authenticate users by either asking for valid login credentials or by checking for valid session cookies.
- The organisation generates a SAML response that contains the authenticated user’s username and other details. In accordance with the SAML 2.0 specification, this response is digitally signed with the organisations’s public and private DSA/RSA keys.
- The organisation encodes the SAML response and the RelayState parameter and returns that information to the user’s browser. The organisation provides a mechanism so that the browser can forward that information to CompliSpace’s ACS. For example, the organisation could embed the SAML response and destination URL in a form and provide a button that the user can click to submit the form to CompliSpace. The organisation could also include JavaScript on the page that automatically submits the form to CompliSpace.
- CompliSpace’s ACS verifies the SAML response using the organisation’s public key. If the response is successfully verified, ACS redirects the user to the destination URL.
- The user has been redirected to the destination URL and is logged in to CompliSpace PolicyPlus.
PolicyPlus Sections & Sitecode Example:
Access | Group/Permission Name | Access Type |
|---|---|---|
| Site Access | Fundamentals | This permission is required to allow any kind of access. Without this permission, no access will be granted whatsoever regardless of other permisions. |
| Public | Public RO | Read Only to the Public section. |
| Public | Public RW | Read and Write to the Public section. |
| Tools Admin | Tools Admin RO | Read Only to the Tools Admin section. |
| Tools Admin | Tools Admin RW | Read and Write to the Tools Admin section. |
| Archived Pages | Archived Pages RO | Read Only to the Archived Pages section. |
| Archived Pages | Archived Pages RW | Read and Write to the Archived Pages section. |
| HR Administration (Managers Only) | HR Administration (Managers Only) RO | Read Only to the HR Administration (Managers Only) section. |
| HR Administration (Managers Only) | HR Administration (Managers Only) RW | Read and Write to the HR Administration (Managers Only) section. |
| Warning |
|---|
Technical Notes for client:
|